Over the past year, hackers have developed a highly effective phishing technique to exploit users of Gmail, G Suite (formerly Google Apps for Work), and other services. They have had great success with this Gmail phishing technique because it is so insidious that even technical users get fooled. The WordPress security experts at Wordfence published a great article about it today. However I’m going to give you the tl;dr version so you can take action NOW to avoid falling victim to such an attack.
How It Works
Here is the timeline of a typical Gmail phishing attack:
- You receive an email in your Gmail inbox. It may be from someone you know (whose account has been hacked) and it may include an image of a familiar-looking attachment.
- You click on the image, expecting Gmail to give you a preview of the attachment. Instead, a new tab opens up and you are prompted to sign in again. You glance at the location bar and you see accounts.google.com in there. It looks like this:
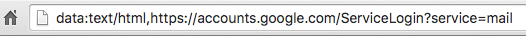
- You go ahead and sign in on a perfectly legitimate-looking sign-in page:
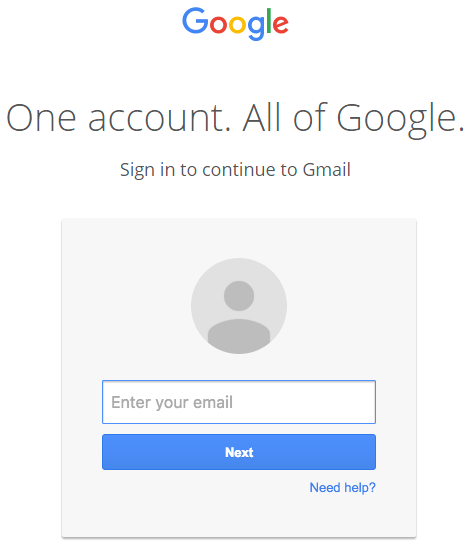
- Once you complete sign-in, your account has been compromised. The hackers have full access to all your emails including sent and received. Armed with your email address, they can also compromise many other services that you use by simply resetting your password.
Why It Works
The technique works so well because humans don’t really notice the ‘data:text/html’ in the location bar. It is the same color as ‘accounts.google.com’, so it appears to be related to the legitimate and trusted hostname of Google. Therefore it doesn’t trigger any red flags in your brain. Read more about Content Blindspots.
How to Protect Yourself
You can protect yourself from Gmail phishing by verifying the protocol and hostname whenever you sign in to a service. For example, when signing into Gmail or G Suite (formerly Google Apps for Work), the location bar should look like this in Chrome:
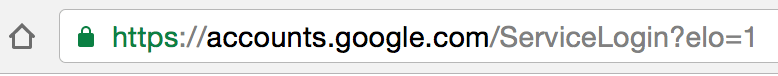
Make sure there is nothing before the hostname ‘accounts.google.com’ other than the green lock symbol and ‘https://’. If you can’t verify the protocol and the hostname, STOP and consider what you just clicked on to get to that sign-in page.
If possible, enable two-factor authentication on every service that you use, such as MailChimp, Facebook, Google, Apple, and WordPress. It usually consists of adding your phone number so the service can text you a verification code. This makes it much more difficult for an attacker to sign in to your account, even if they have already stolen your password. Click here to enable 2-step verification on Gmail.
Not sure if your favorite service supports two-factor authentication? Find out here.
Bottom Line
Be extremely careful about opening email attachments, even from people you know. Just like when you’re driving a car, always check to make sure the “light is green.” A little extra caution can save you a whole lot of heartache down the road. Hackers are always inventing new techniques to prey on the unsuspecting. It’s important to stay alert when using the Internet.

Thanks for the terrific post